15
FebAzure Application Gateway Vs Azure Load Balancer
Azure Application Gateway and Azure Load Balancer are two distinct load-balancing services provided by Microsoft Azure, each designed to address specific traffic management needs in cloud environments. Azure Application Gateway manages and routes HTTP/HTTPS traffic to web applications. Whereas, Azure Load Balancer distributes incoming network traffic across multiple virtual machines (VMs) or services based on IP address and port. While both aim to distribute traffic and improve reliability, they serve distinct purposes and operate at different layers of the OSI model.
Azure Application Gateway vs Azure Load Balancer: Quick Comparison
Before diving into the detailed article, here's a quick side-by-side comparison of Azure Application Gateway and Azure Load Balancer to help you understand their core differences at a glance.
| Feature | Azure Application Gateway | Azure Load Balancer |
| Layer | Layer 7 – Application Layer | Layer 4 – Transport Layer (TCP/UDP) |
| Protocol Support | HTTP, HTTPS, WebSocket | TCP, UDP |
| Traffic Routing | URL path, host headers, request content | IP address and port |
| SSL Termination | Provide SSL termination | Does not provide SSL termination |
| Web Application Firewall | Built-in WAF available | Not supported |
| Session Affinity | Cookie-based | Not Supported |
| Use Case | Web apps, APIs, secure content routing | VM workloads, databases, non-HTTP traffic |
| Cost | Higher (advanced features like WAF, SSL offload) | Lower (basic L4 functionality) |
What is Azure Application gateway ?
Azure Application Gateway is a Layer 7 (Application Layer) load balancer and web traffic manager offered by Microsoft Azure.
- It is designed to make routing decisions based on additional attributes of an HTTP/HTTPS traffic to web applications based on URL paths, host headers, or session affinity.
- Unlike traditional load balancers that work at the transport level, Application Gateway provides intelligent request routing, SSL termination, and Web Application Firewall (WAF).
- Application Gateway is used with Web Application Firewall (WAF) for a scalable and secure way to manage traffic to your web applications.
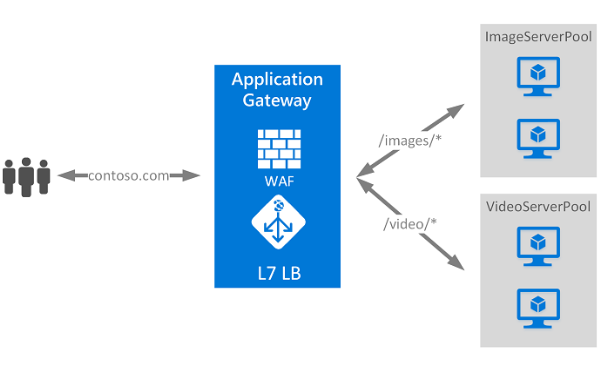
This image shows how Azure Application Gateway works with path-based routing:
- Users access a website (e.g., contoso.com) and send requests.
- Requests first go through the Application Gateway, which includes a Web Application Firewall (WAF) for security.
- The gateway functions as a Layer 7 Load Balancer (L7 LB), inspecting HTTP requests.
- Path-based routing directs /images/* requests to the ImageServerPool.
- /video/* requests are sent to the VideoServerPool, ensuring efficient resource usage.
Features of Azure Application Gateway
- URL-Based Routing: URL Path-Based Routing allows the routing of traffic to backend server pools based on the URL paths of incoming requests.
- Multi-Site Hosting: Application Gateway Hosts multiple websites on a single Application Gateway instance by routing based on domain names. This enables efficient topology configurations for deployments with up to 100+ websites on a single gateway.
- SSL /TLS Termination: Azure Application Gateway supports SSL/TLS termination, Decrypts incoming SSL traffic at the gateway, reducing the processing load on backend servers. The option for end-to-end SSL/TLS encryption is available for applications that demand secure connections due to compliance or security requirements.
- Autoscaling: The Standard_v2 version of Application Gateway supports autoscaling, automatically adjusts the number of gateway instances based on traffic load. This eliminates the need to specify a deployment size or instance count during provisioning.
- Zone Redundancy: Distributes the gateway across multiple availability zones for higher reliability. This eliminates the necessity of provisioning separate gateways in each zone.
Components of Azure Application Gateway:
- Frontend IP Configuration: This is the entry point for incoming traffic. You can configure a public IP address for internet-facing applications, a private IP address for internal applications, or both.
- Listeners: Listeners are logical entities that check for incoming connection requests. They are configured with a frontend IP address, protocol, and port number to accept traffic from clients.
- Backend Pools: These are groups of backend servers, such as Azure Virtual Machines, virtual machine scale sets, Azure App Service, or external servers. The application gateway routes incoming traffic to these backend servers.
- HTTP Settings: These settings define how the application gateway communicates with the backend servers. They include configurations like port, protocol (HTTP or HTTPS), cookie-based affinity, and connection draining.
- Request Routing Rules: These rules tie together the listener, backend pool, and HTTP settings. They determine how the application gateway routes traffic based on conditions like URL path or host headers.
Use Case:
- Hosting Web Applications: Route traffic intelligently based on content type, such as /images or /api.
- API Protection: Web Application Firewall (WAF), Protects web applications from common threats like SQL injection, XSS, etc. It is based on rules from OWASP core rule sets.
- Multi-Region Deployment: Distribute traffic between geographically distributed applications for low latency and high availability.
What is Azure Load Balancer?
Azure Load Balancer is a Layer 4 (Transport Layer) load balancing service provided by Microsoft Azure.
- It is designed to efficiently distribute incoming and outgoing TCP and UDP traffic across multiple virtual machines or services within a region to ensure high availability and reliability.
- Unlike Layer 7 load balancers, Azure Load Balancer operates at the network level and does not inspect application-level content.
- It supports both public and internal traffic balancing, making it ideal for internet-facing services as well as internal applications.
- With features like health probes, automatic failover, and port forwarding (NAT), Azure Load Balancer is a cost-effective and high-performance solution for managing network traffic.
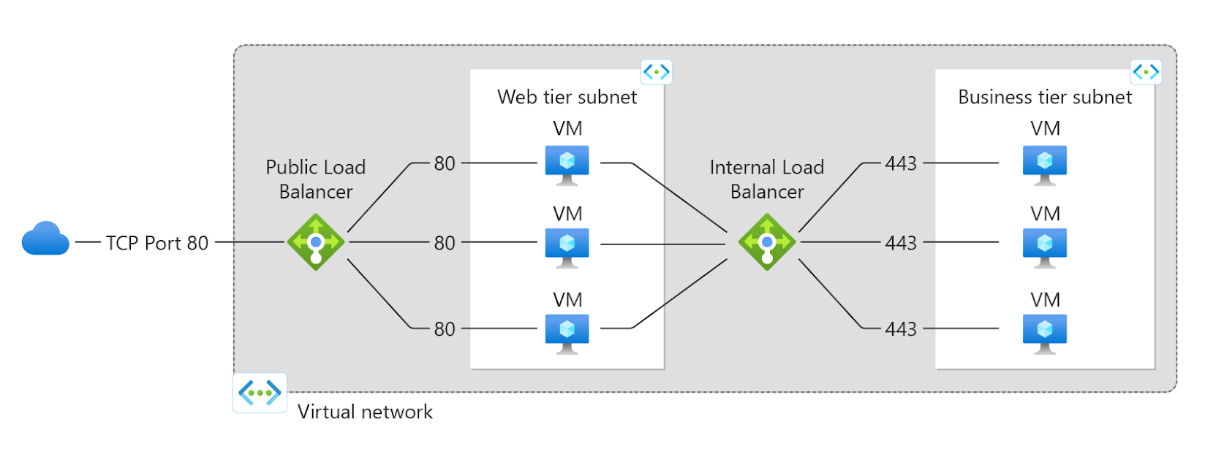
- Users connect to the application via TCP Port 80 through the Public Load Balancer.
- The Public Load Balancer distributes incoming traffic across Virtual Machines (VMs) in the Web tier subnet.
- The Web tier then forwards traffic to the Internal Load Balancer for secure backend communication.
- The Internal Load Balancer routes requests over Port 443 (HTTPS) to VMs in the Business tier subnet.
- This setup separates public-facing and internal services, enhancing security, scalability, and performance.
Features of Azure Load Balancer:
- High Throughput and Low Latency: Supports millions of concurrent connections with extremely low latency, making it suitable for enterprise-grade applications.
- Inbound and Outbound Scenarios: It handles both incoming traffic (from the internet or internal clients) and outgoing traffic (to the internet), efficiently routing it to healthy backend instances.
- Health Probes: Azure Load Balancer uses customizable health probes to monitor the status of backend instances. If a VM becomes unhealthy, traffic is automatically diverted to healthy ones.
- Automatic Failover: In case a backend instance fails, the Load Balancer instantly triggers automatic failover to reroute traffic, ensuring high availability and service continuity.
- Port Forwarding : Enables port forwarding using NAT (Network Address Translation), which allows specific ports of backend VMs to be exposed securely to the internet, useful for services like RDP or SSH.
Use Cases
- Load Balancing Database Clusters: Distributes SQL or NoSQL traffic evenly across database servers to avoid overloading any one node.
- Traffic Management During Maintenance: Ensures uninterrupted service by redirecting traffic when VMs are updated or under maintenance.
- Hybrid Cloud Setups: Azure Load Balancer can route traffic between on-premises infrastructure and Azure-based applications in hybrid environments.
Components of Azure Load Balancer:
1. Frontend IP Configuration: Represents the IP address exposed to clients. Can be: Public IP: For internet-facing load balancers, Private IP: For internal (VNet-only) load balancers.
2. Backend Pool: A set of virtual machines (VMs), scale sets, or instances that receive traffic from the load balancer. Backend pool members are identified by NICs or IP addresses.
3. Health Probes: Used to monitor the health of backend instances. Regularly checks the status using protocols like HTTP, HTTPS, or TCP. If a backend fails the probe, it is automatically removed from load balancing.
4. Load Balancing Rules: Defines how traffic is distributed: Maps frontend IP and port to backend IP and port. Includes protocol (TCP or UDP). Supports session persistence (aka “source IP affinity”).
5. Inbound NAT Rules: Network Address Translation (NAT) rules that allow external traffic to be directed to a specific VM in the backend pool. Typically used for remote desktop (RDP) or SSH access to individual VMs.
6. Outbound Rules: Control outbound internet access from backend instances. Used with Standard SKU Load Balancer to define SNAT (Source Network Address Translation) behavior.
Key Difference Between Azure Application Gateway and Azure Load Balancer:
1. Layer of Operation
- Operates at Layer 7 (Application Layer), focusing on HTTP/HTTPS and WebSockets.
- Inspects packet content to enable advanced routing based on URL paths, host headers, or request attributes.
- Operates at Layer 4 (Transport Layer) of the OSI model, handling TCP/UDP traffic.
- Distributes traffic based on IP address and port number, without inspecting the content of the data packets.
2. Traffic Routing Capabilities
- Offers advanced routing based on URL paths, hostnames, or HTTP headers.
- Supports path-based routing (e.g., /blog to one server, /shop to another) and multi-site hosting (multiple domains on one gateway).
- Provides session affinity (cookie-based) to maintain user sessions on the same backend server.
- Uses hash-based distribution (source IP, destination IP, protocol, and port) to route traffic to backend instances.
- Supports session persistence via 5-tuple or 2-tuple hashing for consistent connections.
3. Security Features
- Includes a Web Application Firewall (WAF) to protect against common web vulnerabilities like SQL injection, cross-site scripting (XSS), and bot attacks.
- Supports SSL/TLS termination (offloading SSL processing to the gateway) and end-to-end SSL for secure communication.
- Provides basic network-level security through integration with Azure Network Security Groups (NSGs) and Azure DDoS Protection.
- Does not inspect or filter application-layer traffic, so it relies on external solutions (e.g., Azure Firewall) for advanced security
4. Scalability and Performance
- Supports autoscaling in the Standard_v2 tier, dynamically adjusting to traffic spikes.
- Offers zone redundancy for high availability across Azure regions.
- Performance is optimized for HTTP/HTTPS workloads but may introduce slight latency due to Layer 7 processing (e.g., WAF inspection, SSL termination).
Azure Load Balancer:
- Optimized for high throughput and low latency, capable of handling millions of connections per second.
- Available in Basic (limited features, no SLA) and Standard tiers (SLA, zone redundancy).
5. Cost Considerations
- Higher cost due to advanced features like WAF, autoscaling, and Layer 7 processing.
- Pricing includes fixed costs (instance hours) and variable costs (data processed, WAF usage).
- Worth the investment for public-facing web applications requiring security and routing flexibility.
Azure Load Balancer:
- Generally lower cost due to its simplicity and focus on Layer 4 balancing.
- Pricing is based on the number of rules and processed data (Standard tier).
- Cost-effective for internal workloads or non-HTTP traffic where advanced features are unnecessary.
When to Use Azure Application Gateway vs Azure Load Balancer
Choosing between Azure Application Gateway and Azure Load Balancer depends on the type of traffic you are managing and your application requirements.
Use Azure Application Gateway When:
- You need to route HTTP/HTTPS traffic based on URL paths, host headers, or request content.
- You want SSL termination to reduce backend server load.
- You need Web Application Firewall (WAF) protection against threats like SQL injection or XSS.
- You're hosting web applications or REST APIs and require intelligent traffic routing.
- You want session persistence (cookie-based affinity) for user sessions.
- Your application is distributed across multiple regions and needs path-based or host-based routing.
Use Azure Load Balancer When:
- You are handling non-HTTP/HTTPS traffic like TCP/UDP, such as RDP, SSH, or database connections.
- You need a fast and simple Layer 4 load balancer for VMs, backend services, or high-throughput applications.
- You want port forwarding (NAT) to expose specific VM ports to the internet.
- You need inbound and outbound traffic handling for workloads in a Virtual Network.
- You're looking for cost-effective and low-latency load distribution.
- You want to ensure VM availability and automatic failover across availability zones.
When to Use Both Azure Application Gateway and Azure Load Balancer
1. Multi-Tier Applications
- Application Gateway manages incoming internet traffic. It offers Web Application Firewall (WAF) protection, SSL termination, and directs traffic to the right web tier.
- Internal Load Balancer balances traffic between application tiers, such as from the web tier to the business tier, using TCP/UDP.
- Azure Load Balancer handles Layer 4 (TCP/UDP) distribution for quick processing and fault tolerance.
- Application Gateway works at Layer 7 (HTTP/HTTPS), allowing for content-based routing, authentication, and thorough request checking.
- Public Load Balancer makes your application accessible on the internet.
- Application Gateway filters and routes HTTP/HTTPS traffic securely before it reaches the backend virtual machines.
- Internal Load Balancer manages traffic between private tiers without public access.
4. High-Security Global Services
- Use geo-based load balancing to guide users to the nearest region.
- Secure all HTTP/HTTPS traffic with Application Gateway WAF, which blocks harmful requests before they reach servers.
- Applications that need TCP load balancing, like databases, VoIP, and game servers, utilize Load Balancer.
- Web and API workloads take advantage of Application Gateway’s routing, SSL offloading, and security policies.
Conclusion
Both Azure Load Balancer and Azure Application Gateway are powerful traffic management tools, each designed for different layers of the OSI model and distinct use cases. Understanding their key differences and strengths helps you choose the right service based on your traffic type, application architecture, and security needs.
Azure Load Balancer functions at Layer 4, whereas Application Gateway handles Layer 7 for more complex traffic routing requirements. In the next 3 years, 75% of developer roles will require Azure expertise. Don’t lag behind. Join our Azure Developer Course now!
FAQs
Take our Azure skill challenge to evaluate yourself!

In less than 5 minutes, with our skill challenge, you can identify your knowledge gaps and strengths in a given skill.