13
FebAzure Firewall - A Comprehensive Guide
Azure Firewall is a fully managed, cloud-based network security solution designed to safeguard resources in your Azure Virtual Network. It operates as a stateful firewall, meaning it tracks active connections and makes intelligent decisions on traffic flow. With features like automatic scaling, high availability, and threat intelligence filtering, it enables you to monitor, control, and protect both inbound and outbound traffic across your cloud environment effectively.
With features like built-in high availability, automatic scaling, and threat intelligence-based filtering, Azure Firewall helps enforce secure traffic flows, detect malicious activity, and ensure compliance with security standards. It also supports application and network-level rules, FQDN filtering, logging, and integration with Azure Monitor for enhanced visibility.
In this Azure tutorial, we will learn crucial concepts related to the Azure firewall, including Firewall Implementation, Firewall setup, Firewall capabilities, Azure firewall vs. NSG, Firewall pricing, Firewall benefits, Firewall use cases, and more. Azure skills are projected to boost your earning potential by 20% in the next 3 years. Enroll now in our Azure Fundamental Free Course with Certification!
Why do we need Network Security in the Cloud Computing?
In today’s digital-first environment, network security is a critical component of cloud computing. As sensitive and mission-critical data increasingly moves to the cloud, organizations must address the unique security challenges that come with cloud infrastructure.
While cloud platforms offer significant benefits—such as scalability, cost-efficiency, and anytime-anywhere access—they also introduce new vulnerabilities that cyber attackers can exploit. Below are key reasons why network security in the cloud is more important than ever:
1. Data Security- Cloud environments host vast amounts of sensitive data, including personal, financial, and corporate information. Robust network security ensures data confidentiality, integrity, and availability by preventing unauthorized access, breaches, and data loss.
2. Reducing Cyber Threats- Cloud platforms are frequent targets of cyberattacks, such as DDoS attacks, ransomware, man-in-the-middle attacks, and insider threats. Effective network security helps identify, block, and mitigate these evolving threats before they cause damage.
3. Shared Responsibility Model- In cloud computing, security is a shared responsibility between the cloud provider and the customer. While providers secure the infrastructure, users must secure their applications, networks, and data. Strong network security measures help fulfill your side of the shared model.
4. Multicloud and Hybrid Environments- As organizations adopt multicloud and hybrid cloud strategies, the complexity of securing data across multiple platforms increases. Network security ensures consistent protection and policy enforcement across environments.
5. Regulatory Compliance- Industries like healthcare, finance, and government must comply with strict regulations (e.g., HIPAA, GDPR, PCI DSS). Implementing robust network security helps meet compliance requirements and avoid legal or financial penalties.
What is the Azure Firewall?
Microsoft Azure Firewall is a fast-faced technology tool and a composed security service that guards your Azure Virtual Network resources. It permits only authorized connections and blocks malicious traffic using threat intelligence. Azure Firewall offers scalability, centralized management, and high availability to ensure protection during failures.
Note: Default Azure Firewall can block all the traffic.
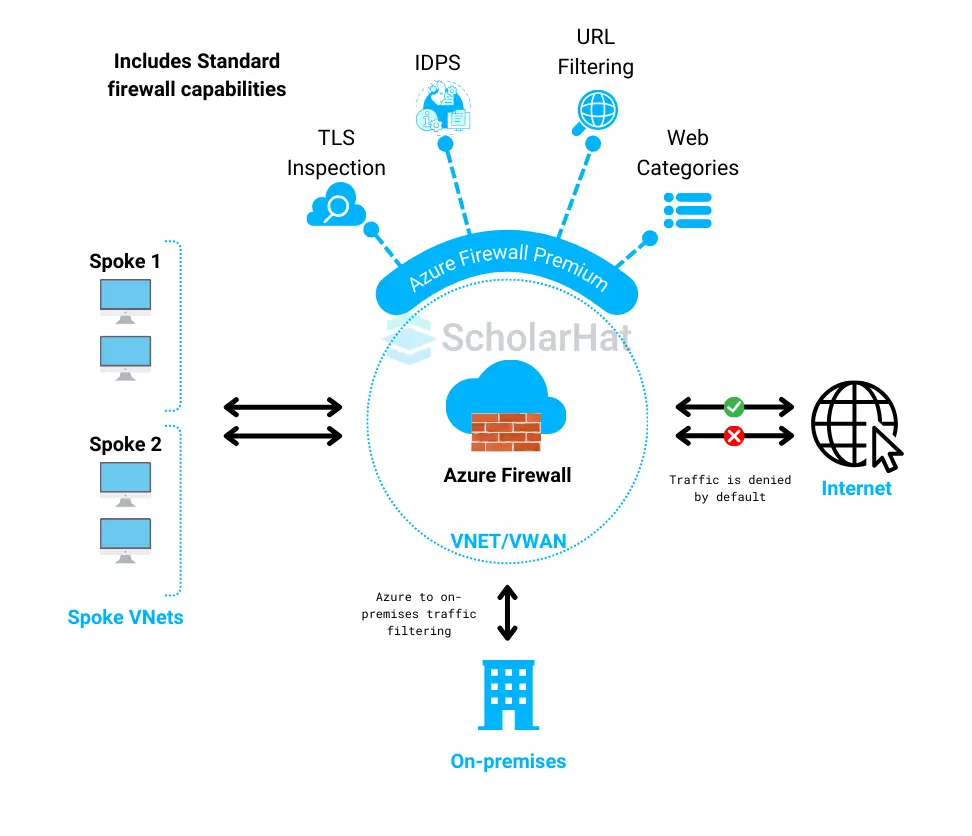
Read More: |
How to set up Azure Firewall?
Here is the complete guidance for setting up Azure Firewall:
1. Preparation
- Identify your needs for protection in your Azure Virtual Network, understand traffic flow, resources requiring security, and your desired security level.
- Create a Resource Group to manage all resources associated with the deployment.
2. Deployment
- Ensure you have a virtual network with subnets :
- Dedicated Azure Firewall Subnet(/26 recommended).
- Workload Subnets(s) for protected resources.
- Set up the Azure Firewall Resource within the Azure Firewall Subnet.
- Allocate a public IP address for the Azure Firewall.
- Create a separate firewall policy resource to define security rules.
2. Configuration
- Specify firewall rules within the policy to allow or deny traffic flow( based on IP address, ports, protocols, and applications (FQDNs).
- Configure a default route in the virtual network to direct traffic to the firewall.
3 Optional Configuration
- Enable threat intelligence for real-time threat filtering.
- Configure web filtering to block access to specific website categories.
- Set up Azure Firewall as a DNS proxy for centralized management and filtering.
- Define custom DNS servers for your virtual network.
- Configure Network Address Translation (NAT) for private addresses to access the internet.
- Implement Forced tunneling (optional) for enhanced outbound traffic security.
4. Testing and Monitoring
- Thoroughly test firewall rules to ensure expected behavior.
- Integrate Azure firewall with Azure Monitor for logging and monitoring network traffic and security.
Azure Firewall Rules:
- Purpose: Control traffic based on IP addresses and ports (Layer 3 and 4).
- Used for: Allowing or blocking specific protocols (like TCP, UDP).
- Example: Allow TCP traffic from a virtual network to an external IP on port 443 (HTTPS).
2. Application Rules
3. NAT Rules (Network Address Translation)
Azure Firewall provides robust capabilities for application rules and URL filtering. Here’s an overview of how to implement these features:
Application Rule Filtering in Azure Firewall
Application rules allow you to control outbound traffic from your Virtual Machines(VMs)to specific FQDNs (Fully Qualified Domain Names) based on the HTTP, HTTPS, and MSSQL protocols.
1. Create an Azure Firewall
- In the Azure gateway, drive to "Create a resource" > "Networking" > "Firewall."
- Configure basic settings, networking, and management.
2. Create an Application Rule Collection
- Go to your Azure Firewall.
- Under "Settings", select "Rules".
- Click "+ Add a rule collection."
- In the "Add rule collection" area, set:
- Name: Set a descriptive name for the rule collection.
- Priority: An integer value refers to the priority of the rule collection (lower numbers have higher priority).
- Action: Select "Allow" or "Deny".
3. Add Rules to the Application Rule Collection
- Click "+ Add a rule" to add a rule to the collection.
- Set the following for each rule:
- Name: A descriptive name for the rule.
- Source type: Set this to "IP address" or "Service Tag."
- Source: Specify the source IP addresses or service tags.
- Protocol: Select the protocol (HTTP, HTTPS, or MSSQL).
- Target FQDNs: Specify the FQDNs to which the rule will apply.
4. Deploy the Application Rule Collection
- Save the rule collection, and it will be applied to your Azure Firewall.
URL Filtering in Azure Firewall
URL filtering allows you to control outbound traffic based on specific URLs and categories. This feature requires enabling Azure Firewall Premium.
1. Upgrade to Azure Firewall Premium
- In the Azure gateway, drive to your actual Azure Firewall.
- Under "Settings", select "Upgrade".
- Follow the prompts to upgrade to Azure Firewall Premium.
2. Create a URL Filtering Rule Collection
- Go to your Azure Firewall Premium.
- Under "Setting," select "Rules."
- Click "+ Add a rule collection."
- In the "Add rule collection" area then, set:
- Name: Set a descriptive name for the rule collection.
- Priority: An integer value refers to the priority of the rule collection (lower numbers have higher priority).
- Action: Select "Allow" or "Deny".
3. Add Rules to the URL Filtering Rule Collection
- Click "+ Add a rule" to add a rule to the collection.
- Set the following for each rule:
- Name: A descriptive name for the rule.
- Source type: set this to "IP address" or "Service Tag."
- Source: Specify the source IP addresses or service tags.
- Protocol: Select the protocol (HTTP or HTTPS).
- URL Categories: Specify the URL categories or individual URLs to filter.
4. Deploy the URL Filtering Rule Collection
- Save the rule collection, and it will be applied to your Azure Firewall Premium.
Difference Between Azure Firewall and NSG
| Feature | Azure Firewall | Network Security Groups (NSG) |
| Service type | Managed Firewall Service | Stateful Firewall |
| Service level | Advanced (L3, L4, L7) | Basic (L3, L4) |
| Threat intelligence | Yes | No |
| SNAT/DNAT | Yes | No |
| Application Security | Yes (L7 inspection) | No |
| Cost | Higher | Less |
| Complexity | Higher | Less |
Features and Benefits of Azure Firewall
Azure Firewall is a structured, cloud-based network security service that safeguards your Azure Virtual Network resources. It offers a comprehensive set of features that translate into benefits for your cloud environments.
Features of Azure Firewall
1. High-Availability
- It provides high availability to increase availability uptime to 99.99%.
- You can deploy a Firewall in an Availability Zone at no additional cost, but there is the cost of outbound and inbound traffic data transfer associated with availability zones.
2. Stateful Inspection
- Analyzes ongoing network connections to differentiate between legitimate traffic and potential threats.
3. Multi-layered Threat Protection
- Filters Traffic at layers 3(Network), 4(Transport), and 7(Application) for control.
- Includes application protocol filtering, URL filtering, and even deep packet inspection.
4. Web Application Firewall
- Protects yourAzureWeb Applications for typical web applications from common attacks like SQL injection and cross-site inspection.
5. Multiple Public IP Address
- It can support multiple IP Addresses.
- This enables the following scenarios:
- DNAT:You can translate multiplied standard port instances over your backend servers.
- SNAT: It supports replacing private IP Addresses, port management, and scalability.
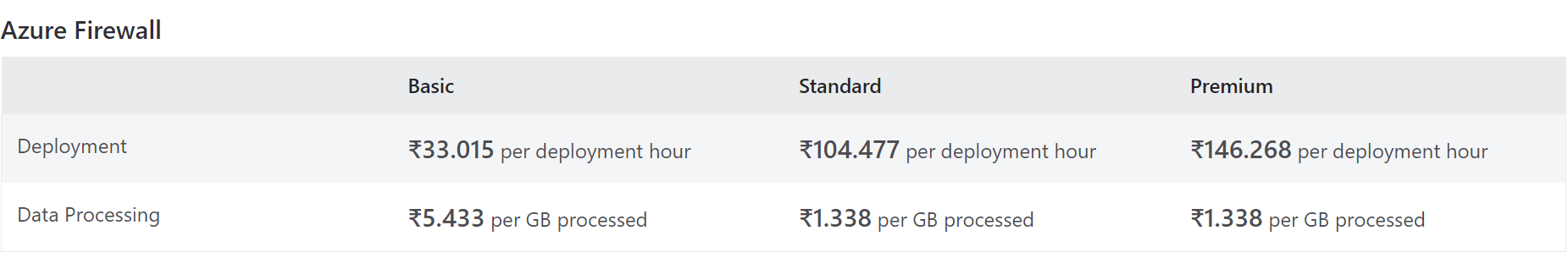
6. Pricing and SLA of Azure Firewall
- Setting up a firewall is easy, with billing involved in fixed and variable fees.
Benefits of Azure Firewall
Azure Firewall offers robust, cloud-native protection for your Azure environment, going beyond basic traffic filtering. Here are the key advantages of using Azure Firewall in your cloud infrastructure:
1. Advanced Threat Protection- Azure Firewall provides deep packet inspection and threat intelligence-based filtering, helping detect and block known malicious IP addresses, domains, and URLs — offering real-time protection against evolving cyber threats.
2. Centralized and Simplified Management- You can centrally manage network and application-level security policies across all Azure Virtual Networks (VNets), making it easier to enforce consistent security rules in large-scale or multi-subscription environments.
3. Reduced Dependence on On-Premises Security- By using Azure Firewall as a cloud-native solution, you may eliminate or reduce the need for traditional hardware firewalls, simplifying your infrastructure and reducing maintenance costs.
4. Built-in Scalability- Azure Firewall is fully elastic and automatically scales to meet the demands of your cloud workloads — ensuring high performance even during traffic spikes or as your environment grows.
5. Enhanced Network Visibility-With integration into Azure Monitor, Log Analytics, and Microsoft Sentinel, Azure Firewall delivers real-time insights into traffic patterns, security rule hits, and potential threats, supporting better network analysis and incident response.
6. Regulatory Compliance Support- Azure Firewall helps organizations meet industry-specific compliance standards like PCI DSS, HIPAA, and GDPR by enforcing strict access controls, traffic inspection, and secure logging.
Azure Firewall Basic vs Standard
| Feature | Azure Firewall Basic | Azure Firewall Standard |
| Target Use Case | Small and medium businesses (SMBs) | Enterprises, larger workloads |
| Performance (Throughput) | Up to 250 Mbps | Scales beyond 30 Gbps |
| Deployment Size | Small scale, limited rules | Large-scale, complex networks |
| Availability | Built-in HA (High Availability) | Built-in HA with auto-scaling |
| Threat Intelligence | Not available | Available (Microsoft Threat Intelligence feed) |
| TLS Inspection | Not supported | Supported |
| FQDN Filtering | Supported | Supported |
| Application & Network Rules | Supported | Supported |
| NAT Rules | Supported | Supported |
Use cases of Azure Firewall
- Web Application Protection- Works with Azure Web Application Firewall (WAF) to secure web applications at both the network (Layer 3/4) and application (Layer 7) levels, defending against external threats and malicious traffic.
- Database Security- Restricts access to database servers by allowing connections only from trusted IP addresses or subnets, preventing unauthorized access and potential data breaches.
- Virtual Network Segmentation- Enables separation of workloads such as internal services and public-facing applications using custom rule collections, improving security through micro-segmentation.
- Environment Isolation- Ensures isolation between development, testing, and production environments by controlling traffic flow, minimizing the risk of cross-environment vulnerabilities or accidental exposure.
- Outbound Traffic Control- Filters and monitors outbound internet access, allowing only approved destinations to prevent data exfiltration and improve compliance with organizational policies.
- Zero Trust Implementation- Supports Zero Trust security models by enforcing least-privilege access, strict traffic controls, and visibility into all network communication—both internal and external.
Conclusion
In the above article, we discussed Azure Firewall, including firewall setup and services used in different industries and business applications. This article will definitely help you understand the steps and regulations to secure your Azure services.
Microsoft Azure Developer Certification holders earn up to ₹12 LPA. Secure your future with our Microsoft Azure Developer Certification Course now.
FAQs
- Azure Firewall focuses on protecting your entire virtual network by inspecting traffic at multiple layers.
- Azure WAF shields web applications from web-specific attacks.
- Destination Network Address Translation (DNAT) Rules.
- Network Rules
- Application Rules
Take our Azure skill challenge to evaluate yourself!

In less than 5 minutes, with our skill challenge, you can identify your knowledge gaps and strengths in a given skill.









