26
DecTop 50+ Microservices Interview Questions and Answers 2025
Microservices Interview Questions
Microservices are a software architectural style in which an application is divided into small, loosely coupled services that can be developed, deployed, and maintained independently. Whether you work with Python, Java, or some other technology, you can still find yourself on a team dealing with microservices. So while interviewing interviewer may ask you some microservices interview questionsespecially those related to server-side development.
Considering all these aspects in mind, In this Microservices tutorial, we have prepared a comprehensive guide on the Microservices Interview Questions and Answers. These 50+ Microservices Interview Questions and Answers are well-framed and designed by experts after proper research and analysis. It will help you counter some of the many challenges the interviewers throw in your microservices interviews. Additionally, enrolling in a .NET Microservices Training and Free Microservices course can further strengthen your expertise and boost your confidence for technical interviews.
Basic Microservices Interview Questions and Answers for Beginners
1. What are the main differences between Microservices and Monolithic Architecture?
| Parameters | Monolithic Architecture | Microservice Architecture |
| Basic | It is built as one large system and is usually one code-base | It is built as a small independent module based on business functionality |
| Scale | It is not easy to scale based on demand | It is easy to scale based on demand. |
| Database | It has a shared database | Each project and module has its own database |
| Deployment | A large code base makes IDE slow and build time increase. | Each project is independent and small in size. So overall build and development time gets decreased. |
| Tightly Coupled and Loosely coupled | It is extremely difficult to change technology or language or framework because everything is tightly coupled and depends on each other | Easy to change technology or framework because every module and project is independent |
| Fault Tolerance | The entire application may fail if a part fails | Individual services can fail without affecting others |
| Maintenance | Easier to maintain due to its simplicity | Requires more effort to manage multiple services |
| Technology | Limited technology choices | Freedom to choose the best technology for each service |
2. Name the key components of Microservices.
The major components of a Microservice Architecture are:
- Containers, Clustering, and Orchestration
- IaC [Infrastructure as Code Conception]
- Cloud Infrastructure
- API Gateway
- Enterprise Service Bus
- Service Delivery
Read More: What are Microservices? Advantages and Disadvantages of Microservices Architecture
3. Explain the challenges found in Microservice deployment.
The deployment of Microservice is a great investment in which many things are to be taken care of. The challenges can be both, technical as well as functional.
The functional challenges are:
- Require heavy investment
- Heavy Infrastructure Setup
- Excessive Planning for managing operations overhead
- Staff Selection and maintenance
The various technical challenges that come to the surface are:
- Communication between different microservices in the application.
- Component automation
- Application maintenance
- Configuration Management
- Heavy Operations Overhead
- Deployment Challenges
- Testing and Debugging Challenges
Level up your career with a .Net Microservices Certification | Enroll in a .Net Microservices Certification course now. |
| Course Name | Training Type | Book a FREE Live Demo! |
| .Net Microservices Certification | Live Training | Access your Free Demo |
4. What are the cases when you need to consider microservice architecture?
In the following cases there can be a need to implement Microservices Architecture:
Complex and Evolving Applications
- Microservices are well-suited for complex applications with evolving requirements, where different parts of the system have varying scalability, performance, and deployment needs.
Large Development Teams
- Microservices are beneficial for large development teams working on different parts of an application simultaneously.
- Each team can own and develop a specific microservice independently, using their preferred programming languages, frameworks, and development practices.
Scalability and Performance Requirements
- Microservices enable horizontal scaling by allowing individual services to be scaled independently based on demand.
- This scalability is beneficial for applications with fluctuating workloads or performance-critical components.
Technology Diversity
- Microservices allow organizations to adopt a technology-agnostic approach.
- Where each service can be implemented using different technologies, programming languages, and frameworks based on its specific requirements.
Frequent Releases and Continuous Deployment
- Microservices support continuous integration and continuous deployment (CI/CD) practices by enabling rapid and independent deployment of individual services.
Fault Isolation and Resilience
- Microservices promote fault isolation by encapsulating functionality within independent services.
- This enhances resilience, fault tolerance, and availability in distributed systems.
Third-Party Integration and Ecosystem Compatibility
- Microservices facilitate integration with third-party services, APIs, and external systems by providing well-defined boundaries and interfaces.
Organizational and Business Agility:
- Microservices align with agile development principles
- It enables organizations to respond quickly to changing business requirements, market demands, and competitive pressures.
5. Name three commonly used tools for Microservices.
- WireMock
- Docker
- Hystrix
Read More: Microservices tools: Top microservices tools to manage Microservices
6. Define coupling and how the microservices are coupled.
- Coupling is the extent of interdependence between software modules.
- In simple terms, it represents proximity connected to two modules or routines.
- Any module can be highly coupled (highly dependent), loosely coupled, and uncoupled with other modules.
// Microservice A
public class UserService {
private final OrderService orderService;
public UserService(OrderService orderService) {
this.orderService = orderService;
}
public void processOrder(String userId, String productId) {
// Perform user-related logic
// Delegate order-related logic to OrderService
orderService.createOrder(userId, productId);
}
}
// Microservice B
public class OrderService {
public void createOrder(String userId, String productId) {
// Perform order creation logic
}
} - The microservices are loosely coupled with one another.
7. Which are the popular companies implementing Microservices architecture?
8. Describe the three types of tests for Microservices.
The three types of tests are mentioned below:
- General tests: In this category come the performance and unit tests at the bottom level. Such tests are fully automated.
- Exploratory tests: These tests are performed at the middle level. Usability tests and stress tests fall into this category.
- Acceptance tests: These tests are performed at the top level. Mostly, they are fewer in numbers. The same assists stakeholders in getting an idea of varied software features.
9. Why do Microservices use containers?
Containers are the easiest and most effective method to manage the microservice-based application. There are several reasons to support this:
- Isolation: Containers provide lightweight, isolated environments for running individual microservices. Each microservice can be packaged as a container image along with its dependencies, libraries, and runtime environment.
- Portability: Microservices packaged as containers can be easily moved and deployed across various infrastructure platforms, such as on-premises servers, public clouds, and hybrid environments.
- Consistency: By packaging microservices as container images, organizations can maintain consistent runtime environments and dependencies across different stages of the software development lifecycle.
- Resource Efficiency: Containers are lightweight and consume fewer resources compared to virtual machines (VMs). This resource efficiency is particularly beneficial in microservices architectures with large numbers of services and instances.
- Scalability: Containers support horizontal scaling, allowing organizations to scale individual microservices independently based on demand.
- Lifecycle Management: Containers provide tools and APIs for managing the lifecycle of microservices, including image creation, deployment, versioning, scaling, and orchestration.
- DevOps Practices: Containers align with DevOps practices and enable organizations to automate the software delivery pipeline from development to production.
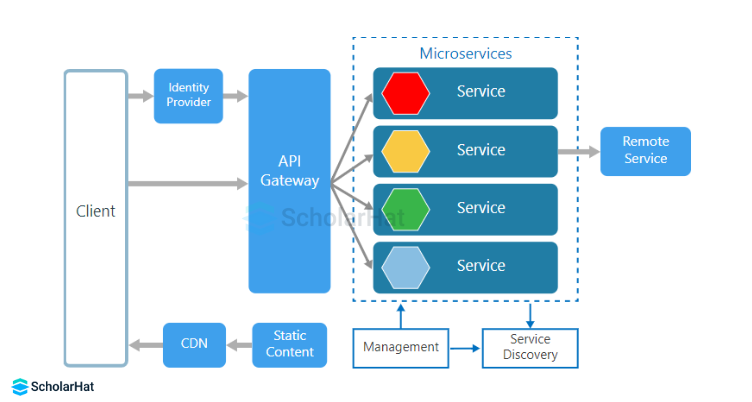
10. What is API Gateway?
API Gateway is an exceptional class of microservices that fulfills the requirement of a single client application. Itacts as a central entry point that handles client requests and then routes them to the appropriate microservices. It serves several purposes:
- Aggregation: The API gateway can combine multiple backend microservices' responses into a single cohesive response to fulfill a client request. This reduces round-trips.
- Load balancing: The gateway can distribute incoming requests across multiple instances of the same microservice to ensure optimal resource utilization and high availability.
- Authentication and authorization: It can handle security-related concerns by authenticating clients and authorizing access to specific microservices.
- Caching: The API gateway can cache responses from microservices to improve performance and reduce redundant requests.
- Protocol translation: It can translate client requests from one protocol (e.g., HTTP/REST) to the appropriate protocol used by the underlying microservices.
11. What is RESTful? What is the role of RESTful APIs in Microservices?
- RESTful also known as REST (Representational State Transfer) web service is an architectural style that assists the computer systems in seamlessly communicating across the Internet.
- Such web services make it easier to understand and deploy microservices.
- A microservice is based on the concept that all its component services interact with one another to complete the business functionality.
- This requires each microservice to have an interface.
- RESTful APIs provide a logical model for building these interfaces.
- It is based on the open networking principles of the Web.
- Thus, it serves as the most critical enabler of microservices.
12. What is end-to-end testing of Microservices? How to implement it for microservices applications?
- End-to-end testing authenticates every workflow process to ensure everything works flawlessly.
- The corresponding tests can encompass the gaps during integration testing or unit testing.
- Also, it makes sure that the network parameters are properly configured and facilitates the advancement of microservices.
Implementing end-to-end testing involves:
- Test data preparation: Prepare a set of test data representing different scenarios and expected outcomes.
- Test environment setup: Set up a test environment that closely resembles the production environment, including the necessary microservices and databases.
- Test orchestration: Create test scripts that simulate user interactions and exercise the application's end-to-end flow, including API calls between microservices.
- Test frameworks: Use testing frameworks like Selenium for frontend testing and tools like Postman or RestAssured for API testing.
- Mocking: Mock external services or use service virtualization to simulate dependencies and external interactions during testing.
- Automation: Automate end-to-end tests to enable continuous testing and faster feedback during development.
- Data cleanup: Implement data cleanup mechanisms to reset test data after each test run to ensure test independence.
13. What Is Spring Boot? How to implement Microservices using Spring Boot?
- Spring Boot is an open-sourced, Java-based framework that provides an excellent platform for developing a stand-alone and production-grade spring application.
- It is easy to understand, increases productivity, and reduces development time.
- It automatically configures a claim based on the added dependencies of an application.
To implement microservices using Spring Boot:
- Set up Spring Boot project: Create a new Spring Boot project using the Spring Initializr or your preferred IDE.
- Define microservice boundaries: Identify distinct functionalities and boundaries for each microservice.
- Create microservices: Implement each microservice as a separate module in the Spring Boot project.
- Define APIs: Design RESTful APIs for intercommunication between microservices and external clients.
- Use Spring Data JPA: Use Spring Data JPA to interact with databases and simplify data access.
- Implement business logic: Write business logic for each microservice, keeping them independent and focused on specific tasks.
- Implement security: Secure microservices with Spring Security, including authentication and authorization mechanisms.
- Dockerize microservices: Containerize microservices using Docker to ensure consistency and portability.
- Implement service discovery: Use Spring Cloud for service discovery, allowing microservices to find and communicate with each other.
- Use circuit breaker: Implement the circuit breaker pattern using Spring Cloud Circuit Breaker to handle service failures gracefully.
- Configure load balancing: Configure load balancing to distribute traffic between instances of microservices using Spring Cloud Load Balancer.
- Monitor microservices: Use Spring Boot Actuator and other monitoring tools to collect metrics and manage microservices effectively.
14. What is Spring Cloud?
- Spring Cloud is a short-lived microservices framework useful for rapidly building applications capable of processing fixed amounts of data.
15. What are the problems that Spring Cloud can solve?
Spring Cloud can deal with the following problems:
- Redundancy issues occurring in distributed systems
- Network issues, bandwidth issues, latency overhead, and security issues
- Stabilizing the allotment of load amongst resources like CPU, network links, clusters, etc
- Service discovery issues to guarantee flawless communication amid services in a cluster
- Performance issues arising due to operational overheads
16. What is an Actuator?
- The actuator is primarily used to render operational information regarding the various parameters of a running application.
- These parameters are metrics, health, dump, info, env, etc.
- For smooth interaction, it makes use of JMX beans or HTTP endpoints.
17. What is the need for reports and dashboards in Microservices?
Reports and dashboards are useful for monitoring and maintenance of microservices.
Multiple tools are available to accomplish this purpose. Reports and dashboards help to:
- Determine which resources are supported by which Microservices.
- Determine which services are impacted when components are changed or replaced.
- Make documentation accessible at all times.
- Examine the component versions that have been deployed.
- Determine the components' maturity and compliance levels.
18. What are the pros and cons of Microservice Architecture?
Pros of Microservice Architecture:
- Flexibility to use different technologies
- Every microservices work on a single capability
- Guarantees security of each service
- Multiple services are simultaneously developed and deployed
- Supports frequent software releases
Cons of Microservice Architecture:
- Needs more effort from the user end for configuration and other tasks
- Difficult to troubleshoot
- Raises delay because of remote calls
- Difficult to keep up with transaction safety
- Difficult to track data over different boundaries
19. What is Distributed Transaction? What are its associated challenges?
- Distributed Transaction is a situation where a single event leads to the transformation of two or more disconnected sources of data that could not be allocated atomically.
- Transactions are handled by a transaction manager responsible for developing and handling transactions.
- If the transaction involves more than one peer, transaction managers of each peer communicate with each other using subordinate or superior relationships.
In the same way, resources are handled by the resource manager who also coordinates with the distributed transaction coordinator for transaction atomicity and isolation.
Challenges of Distributed Transactions:
- Maintaining transactional consistency across multiple services and databases.
- Handling partial failures or rollbacks when one or more services encounter errors.
- Avoiding long-running transactions that may impact system performance and scalability.
- Managing distributed locks and preventing deadlocks.
20. What is OAuth?
- OAuth is the full form of Open-standard Authorization Protocol.
- It is a framework that depicts how distinct services and servers can safely enable authentic access to their assets.
- For the same, there is no need to share the interrelated, single login credentials.
- It is possible to share resources saved on one website with another website; no need to use their credentials.
- OAuth also enables access to the resources from the resource owner.
- It does so by permitting the client applications on third-party providers like GitHub, Facebook, etc.
Microservices Interview Questions for Intermediate
21. What is Continuous Integration (CI) in Microservices?
- Continuous Integration (CI) in microservices is the practice of integrating code changes from multiple developers into a shared repository frequently.
- In the context of microservices architecture, CI involves automating the process of building, testing, and deploying individual microservices to ensure that changes are integrated smoothly and reliably into the system.
22. What is Eureka concerning Microservices?
- Eureka is alternatively famous as the Netflix Service Discovery Server.
- It's an implementation of a service discovery pattern, where microservices can register themselves so others can discover them.
- This server holds information about the client service applications.
- Each microservice registers into the Eureka server and the Eureka server knows all client applications running on each port and IP address.
- It uses the Spring Cloud and is generally recognized as the widely used setup to launch service discovery.
23. Explain Consumer-Driven Contracts.
- Consumer-driven contracts are patterns for evolving services.
- Here, each consumer captures their provider in a separate contract.
- All these contracts are then shared with the provider, which helps them to gain an insight into the obligations they must fulfill for each client.
24. What are the tools for managing a microservice architecture?
The main tools that can be used to build/manage a microservice architecture are:
- MongoDB: It is a document-based open-source distributed database. Here data is stored in JSON format with a different structure for different documents.
- Elasticsearch: It is a full-text search engine.
- KAFKA: It is an event queue system. All transactions are processed via the event queue, thus avoiding the web-like random interactions between different services.
- JENKINS: It is an automation tool that enables Continuous Integration and Continuous Development. It supports many plugins and easily integrates with almost every tool.
- DOCKER: Docker provides a static background for applications to run, thus avoiding deployment issues.
- KUBERNETES: With thousands of services running in an application, Kubernetes, as an engine orchestrates the entire process.
- JAEGER: It is an open-source end-to-end distributed tracing tool. Jaeger monitors distributed transactions, helps in performance optimization, and finds the dependencies between services. It also gives the root cause analysis.
- FLUENT: In a multiservice architecture, where all the different systems are managed via different programming languages and different databases, and run in different operating systems; logging in and keeping track of it is a significant issue. Fluentd provides a single logging layer and simplifies this issue.
- PROMETHEUS: It is a monitoring tool to check if all services are working fine when the application is deployed. It is a time-series data store. It collects metrics from an application and displays them in a graphical format.
- grafana: Grafana provides analytics and monitoring into different visualization formats like graphs, charts, tables, etc.
- NGINX: It acts as a reverse proxy. It acts as a single point entry through which all the API calls are made.
25. What is idempotency and how does it relate to a microservices architecture?
- A method (or API) is idempotent if it can be invoked multiple times with an identical request without having adverse consequences.
- In a microservices architecture, it is recommended to implement retry mechanisms for improved overall resiliency of the system.
- This however can lead to the invoked microservice or consumer receiving more than one identical request.
- If the microservice is not built to be idempotent, this can lead to multiple copies of the same transaction and/or other adverse effects.
- It is therefore important for microservices that expose APIs or consume messages to implement idempotency in a microservices architecture.
26. What is north-south and east-west traffic in Microservices Architecture?
- North-South traffic is the network traffic that flows from external consumers such as end-users, and mobile or web applications.
- East-West traffic in a microservices architecture is the network traffic that flows between internal services or components, such as different microservices within an application.
27. How will you monitor microservices deployments and rollbacks effectively?
We can follow the following approach to monitor microservices deployments and rollbacks:
- Version tracking: Keep a record of the deployed versions of each microservice to track changes and rollbacks accurately.
- Real-time monitoring: Utilize monitoring and observability tools to monitor the performance, health, and error rates of the new deployment.
- Canary deployments: Deploy new versions to a subset of users (canary deployments) to assess their behavior and performance before a full rollout.
- A/B testing: Conduct A/B testing during deployments to compare the performance and user experience of different versions.
- Feature flags: Use feature flags to enable or disable specific features, allowing easy rollbacks by simply toggling the feature flag.
- Automated rollbacks: Set up automated rollback mechanisms triggered by predefined health and performance criteria.
- Post-deployment verification: Perform thorough post-deployment testing to ensure that the new version behaves as expected and meets performance requirements.
28. What are the cases where we cannot use microservices?
1. Small or simple applications: For such applications, a microservices architecture may become an unnecessary complexity and overhead.
2. Early-stage startups: Startups with limited resources and evolving business requirements may benefit from a monolithic architecture. It allows for faster development and easier iteration.
3. Inexperienced team: Implementing microservices requires a good understanding of distributed systems, network communication, and other complexities. If your team lacks experience with microservices, it might be better to start with a monolithic architecture and gradually transition to microservices.
4. Insufficient infrastructure and DevOps capabilities: Effective microservices adoption requires robust infrastructure and DevOps practices. If your organization lacks the necessary infrastructure or DevOps expertise, adopting microservices could be challenging.
5. Inadequate organizational support: Adopting microservices often requires a cultural shift and alignment across development, operations, and business teams. If your organization is not ready for this change, it might be difficult.
29. What is PACT in Microservices Architecture?
- It is an open-source tool that allows testing interactions between service providers and consumers.
- However, it is separated from the contract made.
- This increases the reliability of the Microservices applications.
30. What is Semantic Monitoring?
- Semantic Monitoring or Synthetic Monitoring is running a subset of the application’s automated tests against the live production system.
- These results are monitored, and alerts are generated in case of failures.
- Semantic Monitoring approaches microservice monitoring from the business transaction perspective.
- Instead of monitoring each component, its semantic monitoring ascertains how well the transaction performs for the business and the users.
- It also detects the faulty service layer and the corresponding microservice instance, all at the same flow.
- This approach allows for faster triaging and reduces the meantime to repair.
31. Differentiate Microservices from Containers.
| Aspect | Containers | Microservices |
| Focus | Deployment and isolation of applications. | Architectural approach to building applications. |
| Isolation | Ensures process and file system isolation. | Promotes modularity and independence. |
| Portability | Enables consistent deployment across environments. | Enhances development flexibility. |
| Efficiency | Shares host OS kernel, efficient resource utilization | Supports scalability and autonomy. |
| Rapid Deployment | Quick creation and startup for efficient scaling | Enables independent deployment and scaling |
| Modularity | Not inherently modular | Inherently modular, each service is a component |
| Scalability | Supports scaling applications within containers | Scales individual services based on demand |
| Team Autonomy | Decoupled from application architecture | Teams work independently on services |
| Flexibility | Less flexible in terms of application architecture | Supports diverse technologies per service |
32. What is the Spring Batch Framework?
- Spring Batch is an open-source web framework for batch processing i.e. execution of a series of jobs.
- Spring Batch provides classes and APIs to read/write resources, transaction management, job processing statistics, job restart, and partitioning techniques to process high-volume data.
33. What is Canary Releasing?
- Canary releasing is a technique by which new software versions are introduced by rolling out the updated version to a small subset of users before rolling it out to the entire infrastructure and making it available to everybody.
- This technique is so-called because it is based on canary releases in coal mines to alert miners when the toxic gases reach dangerous levels.
34. What is Mike Cohn’s Test Pyramid?
Mike Cohn’s Test Pyramid describes the type of automated tests required for software development. The Test Pyramid is only a metaphor that implies a grouping of tests based on their granularity. This Pyramid tells which kind of tests should be applied to different levels of the pyramid.
Mike Cohn’s test pyramid consists of three layers that a test suite should have:
- Unit Testing
- Service Testing
- User Interface Testing
We can derive the following two tests from Cohn’s pyramid:
- Define tests with different granularity
- The higher the level you get, the fewer tests you should have.
35. What are the differences between Microservices Architecture and Service-Oriented Architecture (SOA)?
| SOA | Microservices | |
| Implementation | Different services with shared resources | Independent and purpose-specific smaller services |
| Communication | ESB uses multiple messaging protocols like SOAP, AMQP, and MSMQ | APIs, Java Message Service, Pub/Sub |
| Data storage | Shared data storage | Independent data storage |
| Deployment | Challenging. A full rebuild is required for small changes. | Easy to deploy. Each microservice can be containerized. |
| Reusability | Reusable services through shared common resources. | Every service has its independent resources. You can reuse microservices through their APIs. |
| Speed | Slows down as more services are added on | Consistent speed as traffic grows |
| Governance flexibility | Consistent data governance across all services | Different data governance policies for each storage |
Advanced Microservices Interview Questions for Experienced
36. What are the common security vulnerabilities in microservices architecture and how to mitigate them?
The commonly occurring security vulnerabilities in microservices architecture along with their mitigation are as follows:
- Injection attacks: Mitigate by input validation, parameterized queries, and using ORM frameworks that prevent SQL injection.
- Authentication and authorization issues: Implement strong authentication mechanisms and fine-grained access control to prevent unauthorized access.
- Cross-site scripting (XSS): Apply input validation and output encoding to prevent malicious script execution in web applications.
- Cross-site request forgery (CSRF): Use CSRF tokens to verify the legitimacy of requests and prevent unauthorized actions.
- Insecure direct object references: Implement access controls and validate user permissions to prevent unauthorized access to resources.
- Broken authentication: Enforce secure password policies, use secure session management, and implement multi-factor authentication (MFA).
- Security misconfiguration: Regularly audit and review configurations to identify and rectify security weaknesses.
- Data exposure: Encrypt sensitive data, use secure communication protocols (HTTPS), and protect data at rest and in transit.
- Denial-of-service (DoS) attacks: Implement rate limiting, throttle API requests, and use distributed DoS protection services.
- Insecure deserialization: Use safe deserialization libraries and validate incoming data to prevent deserialization attacks.
37. Explain the CQRS pattern.
- CQRS stands for Command Query Responsibility Segregation.
- It allows separate read and write operations.
- It provides multiple benefits such as better performance on read and write sides using the correct technology and scaling read and write sides separately.
- In CQRS, when the write operation persists, an event is stored in the event store.
- This event is used to update the read store asynchronously.
- Events can also be replayed multiple times according to requirements to create different types of query stores.
- As the read store is updated asynchronously at a later time, it will result in an Eventual consistent system.
- Eventual consistency provides high availability and better performance by sacrificing strong consistency.
- CQRS will also eliminate the requirement for distributed transactions if eventual consistency can be accepted.
38. Are microservices limited to backend and middleware or can we develop user interfaces as microservices?
- Microservices are not limited to backend and middleware; you can also develop user interfaces using the microservices pattern.
- This approach is known as Micro Frontends.
- Micro Frontends extend the microservices concept to the front end, breaking down a monolithic application into smaller, independent components.
39. How is synchronous communication advantageous in microservices architecture?
- Services can be built with simple and well-known protocols and frameworks such as REST, gRPC, etc.
- Tight runtime coupling ensures sequential access to services where there is a business workflow implementation
- Each dependent service is called right after another in an ordered way
- Simple and easy request-response mechanism without the need for any broker implementation
40. What are the advantages of using Java for developing microservices?
- Platform independence: Java’s “write once, run anywhere” approach allows microservices to run on any platform supporting the Java runtime.
- Robust ecosystem: Java offers a wealth of libraries and frameworks to support microservices development.
- Scalability: Java allows for easy horizontal and vertical scaling of microservices.
- Strong community support: Java has a large and active developer community, providing support and resources for microservices developers.
- Performance: Java’s Just-In-Time (JIT) compiler enables optimized performance for microservices.
41. How to ensure backward compatibility while rolling out new microservices versions?
- API versioning: Use versioning in APIs to introduce changes without affecting existing clients. Maintain the old version for backward compatibility while deploying the new version to accommodate changes.
- Contract testing: Implement contract testing between microservices to ensure that the new version adheres to the contract defined with its dependencies.
- Semantic versioning: Adopt semantic versioning to communicate the nature of changes in a version. Increment the version number based on the extent of changes: major for backward-incompatible changes, minor for backward-compatible additions, and patch for backward-compatible bug fixes.
- Graceful deprecation: If a feature or API is being deprecated, provide sufficient notice and clear communication to consumers to allow for a smooth transition.
- Feature flags: Use feature flags to control the visibility of new features, enabling them for specific users or gradually rolling them out.
- API evolution: When introducing new fields or parameters, design APIs to tolerate the absence of new fields and provide default values when needed.
42. Explain the principles of the 12-factor app methodology and its relevance to microservices.
- Codebase: Keep your codebase in a version control system, enabling seamless collaboration and tracking changes over time.
- Dependencies: Explicitly declare and isolate dependencies, ensuring consistent environments across development, testing, and production.
- Config: Store configurations in environment variables, promoting flexibility and easy configuration changes without altering code.
- Backing Services: Treat backing services (databases, caching systems) as attached resources, enabling easy replacement and upgrades.
- Build, Release, Run: Strictly separate build, release, and run stages, fostering reliable and repeatable deployments.
- Processes: Execute applications as stateless processes, supporting easy scaling and minimizing conflicts between instances.
- Port Binding: Export services via port binding, ensuring uniform access to applications and seamless communication.
- Concurrency: Scale out by dividing workloads into lightweight, stateless processes, allowing efficient resource utilization.
- Disposability: Maximize robustness with quick startup and graceful shutdown, supporting easy scaling and replacement.
- Dev/Prod Parity: Maintain parity between development and production environments, reducing surprises during deployment.
- Logs: Treat logs as event streams, aiding real-time analysis and debugging in production.
- Admin Processes: Run admin/management tasks as one-off processes, ensuring independence from the main application.
43. Explain the role of Spring Cloud Gateway and how can it be used for API routing and filtering in Java microservices.
Spring Cloud Gateway is a powerful API Gateway built on top of Spring WebFlux, providing essential functionalities for routing and filtering requests in Java microservices. Its role includes:
- API routing: Spring Cloud Gateway acts as an entry point for incoming requests and routes them to the appropriate microservices based on the request path, method, and other criteria.
- Load balancing: It supports client-side load balancing, distributing requests among multiple instances of a microservice using load balancing algorithms.
- Path rewriting: Gateway can rewrite request and response paths, allowing the client to communicate with microservices using a unified URL structure.
- Rate limiting: Spring Cloud Gateway can enforce rate limits on incoming requests, protecting microservices from excessive traffic and potential abuse.
- Security: Gateway can handle security-related concerns, such as authentication and authorization, before forwarding requests to microservices.
- Global filters: It supports global filters that apply to all requests passing through the Gateway, enabling cross-cutting concerns like logging and authentication checks.
- Request and response transformation: Gateway can modify incoming and outgoing requests and responses to adapt them to specific microservices' requirements.
44. What is the Strangler Application?
The Strangler Application pattern involves gradually replacing parts of a monolithic application with microservices.
Example
// Monolithic Service
@RestController
@RequestMapping("/monolith")
public class MonolithController {
@GetMapping("/feature1")
public String feature1() {
return "Monolith Feature 1";
}
@GetMapping("/feature2")
public String feature2() {
return "Monolith Feature 2";
}
}
// Microservice for Feature 1
@RestController
@RequestMapping("/microservices/feature1")
public class Feature1Controller {
@GetMapping
public String feature1() {
return "Microservice Feature 1";
}
}
Explanation
In this setup, the monolithic service and the microservice for Feature 1 are separate components. The monolithic service handles multiple features, while the microservice is responsible for implementing a specific feature (Feature 1) in a more decoupled and independently deployable manner. This division allows for better scalability, maintainability, and flexibility in the architecture.
45. What is Cohesion?
Cohesion measures how closely related the functionalities within a microservice are. High cohesion indicates that a microservice is focused on a specific set of tasks.
// User Service Microservice
@RestController
@RequestMapping("/users")
public class UserServiceController {
private final UserRepository userRepository;
public UserServiceController(UserRepository userRepository) {
this.userRepository = userRepository;
}
@PostMapping
public ResponseEntity createUser(@RequestBody User user) {
User savedUser = userRepository.save(user);
return ResponseEntity.ok(savedUser);
}
@GetMapping("/{userId}")
public ResponseEntity getUserById(@PathVariable Long userId) {
Optional userOptional = userRepository.findById(userId);
return userOptional.map(ResponseEntity::ok)
.orElse(ResponseEntity.notFound().build());
}
@DeleteMapping("/{userId}")
public ResponseEntity deleteUserById(@PathVariable Long userId) {
userRepository.deleteById(userId);
return ResponseEntity.noContent().build();
}
}
In this example, the UserServiceController class represents a microservice responsible for managing user-related functionality. It has three cohesive methods:
- createUser: Handles the creation of a new user by persisting the user data in the database.
- getUserById: Retrieves a user by their ID from the database.
- deleteUserById: Deletes a user by their ID from the database.
All three methods within the UserServiceController class are closely related and focused on user management, demonstrating high cohesion.
46. What are the most common mistakes while transitioning to Microservices?
- Failure to outline the main challenges.
- I am rewriting already existing programs.
- Vague definitions of responsibilities, timeline, and boundaries.
- Failure to identify and implement automation.
47. What are the communication patterns between microservices?
There are two types of communication patterns between microservices:
- Asynchronous Messaging: In this communication pattern, communication between microservices is asynchronous. This is well suited in use cases where the user or system triggering the communication is not waiting for a response.
- Synchronous Messaging (Remote Procedure Invocation):Communication between microservices is synchronous in this communication pattern. i.e. the system or user initiating the communication waits for a response.
48. What is the CAP theorem, and how does it relate to microservices?
The CAP theorem defines the challenges faced in distributed systems, focusing on three fundamental attributes
- Consistency: All nodes in the system see the same data at the same time.
- Availability: Every request receives a response, without guarantee that it contains the most recent version of the information.
- Partition Tolerance: The system continues to operate despite network partitions that prevent communication between some nodes.
CAP Theorem in Microservices: In a microservices architecture, where services communicate over a network, achieving all three attributes simultaneously is challenging. It involves trade-offs, and the system must prioritize two out of the three CAP properties.
49. How do independent Microservices communicate with each other?
Microservices can communicate with each other through:
- HTTP for traditional Request-Response.
- Websockets for streaming.
- Brokers or Server Programs running Advanced Routing Algorithms.
50. Describe the use of APM (application performance monitoring) tools in microservices.
- End-to-end Visibility: APM tools provide end-to-end visibility into the performance of microservices-based applications by monitoring various components and layers of the application stack.
- Service Dependency Mapping: APM tools map out the dependencies between microservices and external services, providing insights into how services interact with each other.
- Distributed Tracing: APM tools use distributed tracing techniques to trace requests as they traverse multiple microservices.
- Performance Monitoring and Alerting: APM tools continuously monitor the performance of microservices in real-time, alerting developers and operations teams about deviations from expected behavior.
- Root Cause Analysis: APM tools facilitate root cause analysis by correlating performance metrics with system events, logs, and infrastructure data.
51. What is service discovery in microservices architecture?
- service discovery is the process by which a microservice searches the network location of another microservice which needs to communicate with.
- Service discovery includes a registry where each service registers itself and looks up others.
- However, Tools such as Eureka, Consul, and Zookeeper are commonly used for service discovery.
52. How does the circuit breaker pattern work in microservices?
- The circuit breaker pattern is used to detect failures.
- It prevents the failure from constantly recurring, allowing the system to maintain performance.
- When a failure threshold is exceeded, the circuit breaker trips and further calls are directed to a fallback mechanism until the service recovers.
53. What are the advantages of using a message broker in microservices architecture?
- Message broker is a part of microservices architecture.
- It facilitates asynchronous communication, decoupling services, improving fault tolerance, and load balancing.
- message broker specifically enables complex workflows.
- There are some Popular message brokers such as RabbitMQ, Apache Kafka, and Amazon SQS.
54. What is the difference between orchestration and choreography in microservices?
- Generally, Orchestration includes a central controller (orchestrator) that manages the interactions between two services.
- While choreography includes each service that interacts with others through events, that too without a central controller.
- Orchestration is more structured as compared to choreography, whereas choreography is more flexible and decentralized.
55. Explain the concept of a bounded context in microservices.
- A bounded context is a central pattern in domain-driven design (DDD) that defines a clear boundary within which a particular model is defined and applicable.
- Each microservice typically represents a bounded context, ensuring that its data and functionality are self-contained and loosely coupled with other services.
56. What is the role of a sidecar pattern in microservices?
- The sidecar pattern is used to deploy a helper service alongside a main service in a separate container but within the same pod in Kubernetes.
- This helper service handles various kinds of tasks such as logging, monitoring, configuration, and networking, enhancing the functionality.
57. How does API versioning work in microservices?
- API versioning works as backward compatibility in microservices by allowing multiple versions of an API to coexist.
- API versioning has methods that include URI versioning (e.g., /api/v1/resource), header versioning (e.g., using a version header), and query parameter versioning (e.g., /api/resource?version=1).
58. What is the significance of eventual consistency in microservices?
- Eventual consistency is nothing but a distributed system, updates to data will propagate and reach a consistent state across all nodes.
- This is critical in microservices to ensure availability and partition tolerance (as per the CAP theorem) while accepting temporary inconsistencies.
59. What are sagas in microservices architecture?
- Sagas are a pattern for managing distributed transactions in microservices.
- A saga is a sequence of local transactions, where each step is completed and followed by a compensating action in case of failure, ensuring eventual consistency across services.
60. How do you handle logging and monitoring in microservices?
- It collects logs from multiple services, aggregating them centrally, and analyzing them for insights.
- Tools like ELK Stack (Elasticsearch, Logstash, Kibana), Prometheus, Grafana, and Jaeger are commonly used for centralized logging and distributed tracing.
- It enables efficient monitoring and troubleshooting.
Summary
| Download this PDF Now - Microservices Interview Questions and Answers PDF By ScholarHat |
If you are preparing for the.NET Microservices Interview Questions and Answers Book, this .NET Microservices Interview Questions and Answers Book can really help you. It has simple questions and answers that are easy to understand. Download and read it for free today!
FAQs
- What microservices are, their benefits (such as scalability and flexibility), and their disadvantages (like complexity and data management).
- Learn about important ideas including data management techniques, inter-service communication (gRPC, REST, RabbitMQ, Kafka), service decomposition, and design patterns (API Gateway, Circuit Breaker, Saga).
- Work on projects that make use of frameworks and tools such as Spring Boot, Docker, Kubernetes, and service discovery tools like Consul or Eureka to get hands-on experience.
- What are microservices and how do they differ from monolithic architectures?
- What are the key benefits and drawbacks of using microservices?
- Explain the concept of service decomposition.
- What is an API Gateway and what role does it play in a microservices architecture?
- How do you ensure data consistency in a microservices environment?
- What are some common design patterns used in microservices?
- How do you handle inter-service communication?
- What are the challenges of implementing microservices?
- Explain the Circuit Breaker pattern.
- What is eventual consistency and how is it achieved in microservices?
- Design a microservices architecture for an e-commerce application.
- How would you implement inter-service communication in a microservices setup?
- Describe a strategy for handling failures and retries in microservices.
- Explain the process of deploying microservices using Docker and Kubernetes.
- How would you implement security in a microservices architecture?
- Describe your experience with monitoring and logging in a microservices environment.
- How do you handle transactions across multiple microservices?
- Explain a blue-green deployment strategy.
- How do you scale microservices to handle increased load?
- Describe a scenario where you had to troubleshoot a microservices-related issue.
Take our Microservices skill challenge to evaluate yourself!

In less than 5 minutes, with our skill challenge, you can identify your knowledge gaps and strengths in a given skill.