06
FebTop 50 Solution Architect Interview Questions
Solution Architect interview questions are designed to evaluate a candidate’s ability to design, implement, and manage complex software solutions that are scalable, secure, and aligned with business objectives.
In this Software Architecture Tutorial, Solution Architect interview questions and answers, from core concepts like microservices, APIs, and cloud architecture to advanced and future-focused topics such as AI integration, serverless systems, and digital twins are covered . Future-proof your career! Learn Azure for free, earn a certificate, and move closer to high-paying architect roles. Enroll now in our Free Azure AI Fundamentals Course.
Solution Architect Interview Questions and Answers for Freshers
If you’re aiming to start your career as a Solution Architect, these questions will help you build strong fundamentals. Let’s begin with Solution Architect Interview Questions and Answers for Freshers.
1. What are the Core Principles of System Design?
The core principles of system design are:
- Scalability: Design the system to handle increasing amounts of traffic or data smoothly, using techniques like load balancing, caching, and horizontal scaling.
- Reliability: Ensure the system remains available and functions correctly even under failures, using redundancy, replication, and failover strategies.
- Maintainability: Build the system in a modular and organized way so that it can be easily updated, debugged, or extended without major rewrites.
- Performance: Optimize for speed and efficiency, ensuring fast response times, minimal latency, and effective use of resources.
- Consistency: Guarantee that data remains accurate and reliable across all components, using appropriate consistency models and transaction management.
2. What is the role of a solution architect in a software development project?
The role of a Solution Architect (SA) in a software development project is to design and oversee the overall technical solution, ensuring it meets both business and technical requirements.
Roles and Responsibilities of a Solution Architect are:
- Requirement Analysis: Understand business needs and translate them into technical solutions.
- System Design: Define overall architecture, choose technologies, and ensure scalability, security, and maintainability.
- Technical Leadership: Guide development teams on best practices and design patterns.
- Integration: Ensure smooth interaction with existing systems and third-party services.
- Risk Management: Identify technical risks and make trade-off decisions.
- Documentation & Communication: Create architecture diagrams and communicate design clearly.
| Training Name | Training Mode | Get Free Demo!! |
| Java Solution Architect Certification | Live Training | Book a FREE Demo Now! |
| .NET Solution Architect Certification | Live Training | Book a FREE Demo Now! |
3. Explain the difference between a solution architect and a technical architect?
| Aspect | Solution Architect(SA) | Technical Architect(TA) |
| Focus | Focuses on the overall solution, ensuring it meets business goals and technical requirements. | Focuses on the technical implementation, ensuring components are efficiently designed and implemented. |
| Scope | Designs the big-picture architecture, including system integration, workflows, and technology stack selection. | Designs component-level architecture, detailing frameworks, databases, and internal technical processes. |
| Responsibilities | Translate business needs, choose tech stack, ensure scalability and security | Guide developers, optimize code, ensure reliability |
| Perspective | Balances business objectives with technology decisions to align the solution with organizational goals. | Focuses purely on technical feasibility, optimization, and execution of the solution. |
| Decision Level | High-level architectural decisions | Detailed technical/design decisions |
| Example | Deciding microservices, cloud deployment, API strategy | Choosing frameworks, database schemas, caching, component optimization |
4. What Specific Skills does a Solution Architect require?
The core skills of a Solution Architect:
- System Architecture: Design scalable, reliable, and maintainable solutions.
- Cloud & Infrastructure: Expertise in AWS, Azure, or GCP deployment.
- Databases & Integration: SQL/NoSQL, APIs, and service interoperability.
- Security: Implement authentication, authorization, and data protection.
- Business & Requirement Analysis: Translate business needs into technical solutions.
- Decision Making & Risk Management: Make trade-offs and mitigate technical risks.
- Leadership & Communication: Guide teams and collaborate with stakeholders.
- DevOps & Monitoring: Understand CI/CD pipelines, deployment, and observability.
5. What is AWS?
AWS (Amazon Web Services) is a comprehensive cloud computing platform provided by Amazon. It offers a wide range of on-demand cloud services like computing power, storage, databases, networking, machine learning, and analytics, allowing individuals and organizations to build and manage applications without owning physical infrastructure.
6. What is Domain Driven Design?
Domain-Driven Design (DDD) is a software development approach that focuses on modeling software based on the business domain and its logic. The main goal is to ensure that the software structure reflects real-world business processes and terminology.
Benefits of DDD:
- It aligns software design closely with business requirements.
- It reduces complexity by dividing large domains into manageable bounded contexts.
- It improves communication between technical and business teams.
- It makes the system more maintainable and scalable.
7. What is the importance of documentation in solution architecture?
Documentation in solution architecture acts as a blueprint and communication bridge, ensuring that the system is built, maintained, and scaled effectively while minimizing risks and misunderstandings.
The importance of documentation in solution architecture are:
- Clear Communication: Helps developers, testers, and stakeholders understand the system.
- Reference for Development & Maintenance: Acts as a blueprint for implementation and future updates.
- Decision Tracking: Records technology choices, trade-offs, and rationale.
- Knowledge Transfer: Onboards new team members quickly.
- Risk & Compliance: Supports security, regulatory compliance, and risk management.
8. What are the goals for a professional solution architect?
The goals of a professional Solution Architect revolve around delivering high-quality, scalable, and business-aligned software solutions.
The key goals are:
- Align technology with business goals to solve real problems.
- Design scalable, reliable, and maintainable systems.
- Ensure security, compliance, and risk mitigation.
- Guide development teams and promote clear communication.
- Optimize performance, cost, and future flexibility.
9. List the tools you may use for designing a solution.
The tools used by Solution Architect are:
- Lucidchart, Draw.io (Diagrams.net), Microsoft Visio – For architecture diagrams, flowcharts, and visual modeling.
- Creately, Miro, MURAL – Collaborative whiteboarding and design planning.
- Visual Paradigm, Enterprise Architect, Astah – UML modeling, ER diagrams, and system architecture design.
- AWS Well-Architected Tool & AWS Icons – Design cloud solutions on AWS.
- Azure Architecture Center, GCP Architecture Diagrams – Cloud-specific solution planning.
- Confluence, Notion, Google Workspace, Microsoft 365 – Document decisions, share specifications, and collaborate with teams.
- Figma, Adobe XD, Sketch – Prototype and visualize user interfaces when needed.
10. What is the major benefit of being a solution architect?
The major benefit of being a Solution Architect is the ability to bridge business and technology, designing systems that solve real-world problems while influencing critical technical and strategic decisions.
Key Benefits of Solution Architect are :
- High Impact Role: Shape the architecture of important projects and influence business outcomes.
- Holistic Perspective: Gain a broad view of technology, processes, and business strategy.
- Career Growth: Opens doors to senior roles like Enterprise Architect or CTO.
- Problem Solving: Work on complex, challenging technical and business problems.
- Leadership Opportunities: Guide teams, mentor developers, and drive decision-making.
11. What is Cloud Computing ?
Cloud Computing is the delivery of computing resources and services over the internet, allowing users to access servers, storage, databases, networking, software, and analytics on-demand, without managing physical infrastructure.
| Read more: Cloud Computing Interview Questions and Answers |
12. How Cloud Computing is important for a Solution Architect?
Cloud Computing is extremely important for a Solution Architect because it provides the foundation to design scalable, flexible, and cost-effective solutions.
Cloud Computing is important for a Solution Architect for:
- Scalability & Flexibility: Easily scale resources up or down.
- Cost Efficiency: Pay-as-you-go reduces infrastructure costs.
- Rapid Deployment: Provision resources quickly for faster delivery.
- Global Availability: Ensure low-latency access worldwide.
- Integration & Services: Leverage databases, AI/ML, analytics, and messaging.
- Resilience & Security: Built-in redundancy, backups, and security.
- Innovation & Experimentation: Prototype and test solutions quickly.
Solution Architect Interview Questions for Intermediate
These intermediate-level questions will test your ability to design scalable, secure, and efficient solutions.
13. Explain the CAP Theorem.
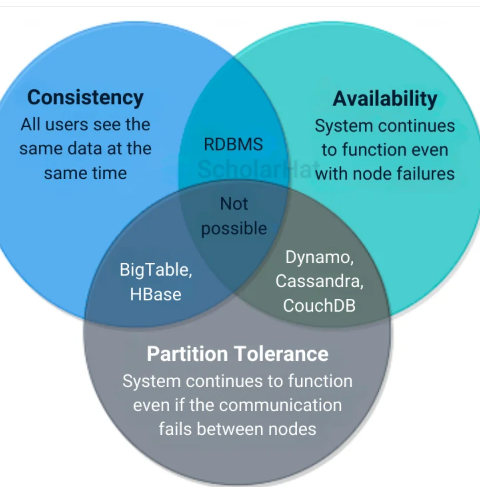
- Consistency (C): All nodes see the same data at the same time.
- Availability (A): Every request gets a response, even if the data is not the latest.
- Partition Tolerance (P): The system keeps working even if some nodes cannot communicate.
14. Explain the difference between asynchronous and parallel programming.
| Aspect | Asynchronous Programming | Parallel Programming |
| Definition | Tasks run non-blocking, allowing other tasks to continue while waiting for completion | Tasks run simultaneously on multiple cores/processors |
| Execution | Often single-threaded, tasks may execute sequentially but don’t block | Multi-threaded or multi-core, tasks execute at the same time |
| Purpose | Improve responsiveness and avoid idle waiting | Improve performance and speed up computation |
| Use Cases | I/O operations, network requests, file reading/writing | CPU-intensive tasks, heavy calculations, data processing |
| Key Benefits | Keeps application responsive | Reduces total execution time for heavy tasks |
15. How do you ensure effective communication between technical and non-technical stakeholders?
Key Strategies to ensure ffective communication between technical and non-technical stakeholders:
- Avoid jargon or technical terms when speaking to non-technical stakeholders.
- Translate technical concepts into business-relevant outcomes.
- Use flowcharts, architecture diagrams, mockups, or dashboards to explain complex ideas.
- Helps stakeholders visualize the system and understand dependencies.
- Schedule consistent check-ins to provide progress updates.
- Use status reports and demos to keep everyone aligned.
- Understand stakeholder priorities, concerns, and expectations.
- Ensure technical decisions align with business needs.
- Maintain clear documentation of architecture, trade-offs, and decisions.
- Serves as a reference for both technical and non-technical teams.
16. What is User Acceptance Testing (UAT)?
Key Points:
- Purpose: Ensure the software satisfies business needs and is ready for production.
- Performed By: Actual end users or business representatives.
- Focus: Functional requirements, workflows, and usability.
- Timing: After system testing, before deployment.
- Outcome: Users approve the system for release or report issues for correction.
17. What do you mean by IaaS, PaaS, and SaaS?

1. IaaS (Infrastructure as a Service):A cloud service that gives you virtual servers, storage, and networking. You control the operating system and applications, but the provider manages the hardware.
- Example: AWS EC2, Google Compute Engine.
- Example: Heroku, Google App Engine.
- Example: Gmail, Microsoft 365, Dropbox.
18. What is load balancing and why is it important?
Load balancing is the process of distributing incoming network traffic across multiple servers so that no single server gets overloaded.
It is important because it:
- Improves Performance: Ensures fast response by preventing any server from becoming too slow.
- High Availability: If one server fails, traffic is sent to another server, keeping the service online.
- Scalability: Makes it easy to add or remove servers as demand changes.
- Reliability: Reduces downtime and provides a smooth user experience.
- Efficient Resource Use: Distributes workload evenly, avoiding underuse of some servers and overload on others.
19. What are some key principles of solution architecture?
Key principles of Solution Architecture are:
- Business Alignment – The solution must support business goals and strategy.
- Scalability & Performance – Should handle growth and provide fast, reliable service.
- Security – Protect data and systems from threats with built-in security measures.
- Maintainability – Easy to update, extend, and manage over time.
- Cost-effectiveness – Balance between performance and budget, both short and long term.
20.What is Microservices Architecture.
21. Explain caching and its role in system performance.
Role of Caching in System Performance
22. What is a database index?
23. What are ACID properties in databases?
ACID properties ensure that database transactions are reliable, consistent, and safe, even in case of errors or failures. ACID stands for:- A transaction is all or nothing. Either all steps succeed, or none do.
- Example: Transferring money from Account A to B – both debit and credit must happen, or neither happens.
- Transactions must take the database from one valid state to another, following all rules and constraints.
- Example: After a transaction, the total balance across all accounts should remain correct.
- Multiple transactions can happen at the same time without interfering with each other.
- Example: Two users booking the same seat should not cause conflicts.
- Once a transaction is committed, the changes are permanent, even if the system crashes.
- Example: After payment is processed, the record remains in the database even if the server fails immediately after.
24. What is the role of APIs in solution architecture?
APIs (Application Programming Interfaces) are the connectors that allow different software components, services, or systems to communicate within a solution architecture. They play a critical role in ensuring modularity, flexibility, and integration.
The role of APIs in solution architecture:
- Integration: Connects different systems and services for seamless communication.
- Loose Coupling: Allows components to interact without depending on internal code.
- Scalability: Enables services to scale independently while communicating efficiently.
- Reusability: Exposes functionality that can be used across multiple applications.
- Security: Controls access through authentication, authorization, and monitoring.
- Flexibility: Allows mixing and matching of services to build modular systems.
25. What is Containerization?
Containerization is a method of packaging an application along with all its dependencies (libraries, runtime, configuration) into a single, lightweight unit called a container. This ensures the application runs consistently across different environments.
26. How do you decide between SQL and NoSQL databases for a project?
The choice depends on the nature of the data, scalability requirements, and use cases. Key considerations:
1. Data Structure
- SQL (Relational): Best when data is structured, tabular, and relationships are important.
- NoSQL (Non-Relational): Suitable for unstructured or semi-structured data like JSON, documents, or key-value pairs.
2. Scalability
- SQL: Scales vertically by adding more power to a single server.
- NoSQL: Scales horizontally by adding more servers, which makes it better for managing very large datasets and high traffic.
3. Transactions & Consistency
- SQL: Strong ACID compliance makes it reliable for financial, banking, and mission-critical apps where data consistency is important.
- NoSQL: Often follows BASE (Basically Available, Soft state, Eventually consistent), which is better for high-speed, distributed apps where eventual consistency is okay.
4. Query Flexibility
- SQL: Works well when complex queries, joins, and analytics are needed.
- NoSQL: Better suited for fast key-based lookups, real-time apps, and flexible schema needs.
5. Use Cases
- SQL: Banking systems, ERP, CRM, inventory management.
- NoSQL: Social media apps, IoT, real-time analytics, content management, recommendation engines.
27. Explain the concept of service mesh and its benefits.
A service mesh is an infrastructure layer in a microservices architecture that controls communication between services. Instead of each microservice handling its own networking, security, and observability, a service mesh offers these functions through a separate layer.
Benefits of a Service Mesh
- Simplifies Microservices Communication: It removes the burden of networking logic from application code.
- Improved Security: It enforces mutual TLS and allows for detailed access control between services.
- Better Observability: It gives architects and developers insights into traffic flow, latency, and failures.
- Consistency Across Services: It offers standardized policies for traffic, security, and monitoring.
- Resilience & Reliability: It ensures services remain available even if some nodes fail.
28. How do you ensure security in your solution design?
Ensuring security in solution design requires a multi-layered approach that addresses risks at every level: infrastructure, application, data, and user access.
Key Steps to Ensure Security:
- Secure Architecture Design: Use defense-in-depth and least privilege principles.
- Authentication & Authorization: Use strong authentication and role-based access control.
- Data Protection: Encrypt sensitive data at rest and in transit.
- Network Security: Use firewalls, VPNs, and zero-trust network segmentation.
- API & Application Security: Validate input and protect APIs with rate limiting and gateways.
- Monitoring & Auditing: Enable logging, monitoring, and regular audits.
- Compliance & Governance: Follow regulations like GDPR, HIPAA, and PCI DSS.
29. What is Middleware, and why is it important in solution design?
Importance in Solution Design
- Simplifies Complex Systems. Developers don’t need to handle low-level networking or integration logic.
- Improves Reusability. Common services like authentication, logging, and messaging can be centralized.
- Increases Flexibility. It becomes easier to replace or upgrade individual components without affecting the entire system.
- Supports Distributed Architecture. This is essential for microservices, SOA, and cloud-native applications.
30. What is the role of CI/CD pipelines in architecture?
CI/CD Role in Solution Architecture:
- Automated Testing: Makes sure code changes get tested automatically for quality and functionality before they are deployed.
- Faster Delivery: Allows for rapid, frequent, and predictable releases to production or staging environments.
- Error Reduction: Cuts down on human errors through automation in building, testing, and deploying applications.
- Consistency Across Environments: Ensures that code behaves the same in development, testing, and production.
- Improved Collaboration: Helps integrate multiple developers’ work smoothly.
31. How do you design multi-tenant applications?
A multi-tenant application lets multiple clients (tenants) use the same software while keeping their data separate and secure.
Simple Design Steps:
- Data Isolation: Use separate databases, separate schemas, or a shared database with tenant IDs.
- Security: Ensure each tenant can only access their own data, and encrypt sensitive information.
- Scalability: Design the system to handle more tenants by adding servers or resources as needed.
- Custom Settings: Allow tenants to have their own features, themes, or configurations.
- Monitoring: Keep track of usage, performance, and errors for each tenant.
Advanced Solution Architect Interview Questions
Let’s move on to some advanced-level questions for Solution Architect Interview.
32. How do you ensure database Sharding and Partitioning is effective?
Key Steps to Ensure Effectiveness
- Choose the Right Shard Key: Select a key (like user ID or region) that evenly distributes data across shards to prevent hotspots.
- Maintain Data Locality: Keep related data together to minimize cross-shard queries, improving query performance.
- Ensure Scalability: Plan for horizontal scaling by adding new shards as data grows without downtime.
- Implement Redundancy & Replication: Use replication to prevent data loss and improve availability across shards.
- Monitor Performance: Track query times, shard sizes, and load distribution to identify imbalances or hotspots.
- Plan for Rebalancing: Have a strategy to redistribute data when new shards are added or old ones become overloaded.
- Maintain Consistency & Transactions: Use appropriate consistency models (ACID or eventual consistency) and transaction strategies across shards.
33. Explain event-driven architecture and when to use it.
Event-Driven Architecture (EDA) is a software design pattern in which components communicate by producing and consuming events instead of calling each other directly. An event represents a significant change or action, such as "order placed" or "payment completed." Components, or services, respond to these events asynchronously. This setup allows for decoupled and scalable systems.
Use Event-Driven Architecture
- Real-Time Applications: For example, live dashboards, stock trading, or IoT systems.
- Microservices Communication: When services need to operate independently and respond to changes asynchronously.
- High Throughput Systems: Applications that handle massive amounts of data or events, like social media feeds or notifications.
- Workflow Automation: Triggering actions based on events, e.g., sending confirmation emails after order placement.
34. What are cloud-native applications, and what advantages do they offer?
Cloud-native applications are software systems designed specifically to run in cloud environments, taking full advantage of cloud services, scalability, and automation. They are typically built using microservices, containers, and APIs, and leverage orchestration platforms like Kubernetes for deployment and management
Advantages of Cloud-Native Applications
- Scalability: Automatically scale resources up or down based on demand.
- Resilience: Built-in fault tolerance and self-healing mechanisms.
- Faster Deployment: CI/CD pipelines enable rapid updates and feature releases.
- Cost Efficiency: Pay-as-you-go cloud resources reduce unnecessary expenses.
- Flexibility & Portability: Containers allow deployment across different clouds or hybrid setups.
- Improved Collaboration: Microservices and DevOps practices allow teams to work independently and efficiently.
35. What is the principle of least privilege, and how do you apply it?
Principle of Least Privilege (PoLP) is a security concept where users, systems, and applications are granted only the minimum access rights necessary to perform their tasks. This minimizes the risk of accidental or malicious misuse of sensitive resources.
To Apply the Principle of Least Privilege:
- Role-Based Access Control (RBAC): Assign permissions based on user roles rather than individuals.
- Time-Bound Access: Grant temporary permissions when needed, and revoke them automatically after the task is completed.
- Segmentation of Duties: Separate critical functions among multiple users to prevent misuse.
- Regular Access Reviews: Periodically audit permissions to ensure they remain appropriate.
36. How do you design role-based access control (RBAC) in an application?
Role-Based Access Control (RBAC) is a method of restricting system access based on user roles, where each role has a set of permissions to perform certain actions.
Key Steps to Design RBAC
- Identify Roles: Define roles based on job functions or responsibilities (e.g., Admin, Editor, Viewer).
- Define Permissions: List the actions or resources each role can access (e.g., read, write, delete).
- Assign Roles to Users: Map users to one or more roles based on their responsibilities.
- Implement Role Hierarchies: Allow higher-level roles to inherit permissions from lower-level roles if needed.
- Use Principle of Least Privilege: Ensure roles have only the permissions necessary for their tasks.
- Audit and Review: Periodically review roles, permissions, and assignments to maintain security.
- Integrate with Authentication: Connect RBAC with authentication systems (SSO, OAuth, JWT) for seamless access control.
37. What is Infrastructure as Code and what are its benefits?
Key Benefits of IaC are:
- Automation: Infrastructure can be provisioned, configured, and managed automatically.
- Consistency: Eliminates configuration drift between development, testing, and production.
- Version Control: Infrastructure changes can be tracked and rolled back like application code.
- Scalability: Easily scale environments up or down by modifying configuration files.
- Faster Deployment: Reduces manual setup time and human errors.
38. How do you choose between REST, GraphQL, and gRPC APIs?
To choose between REST, GraphQL, and gRPC depends on use case, performance needs, client requirements, and complexity of your system.
| Criteria | REST | GraphQL | gRPC |
| Data Fetching | Fixed endpoints; may over-fetch or under-fetch data | Clients specify exactly what data they need | Strictly defined service contracts; efficient binary data |
| Performance | Works well for most web applications; JSON over HTTP | Reduces round-trips but can be complex to implement | High-performance, low-latency, ideal for microservices or streaming |
| Ease of Use | Easy to understand and implement; widely supported | Flexible, but requires learning schema definitions and queries | Requires protocol buffers and client/server stubs |
| Use Case | CRUD operations, simple web/mobile APIs | Complex front-end queries, multiple related entities | Real-time streaming, internal service communication, IoT |
39. How do you design cloud cost optimization strategies?
Cloud cost optimization means lowering cloud expenses while keeping performance and scalability. Solution architects create plans to adjust resources, remove waste, and use cloud-native features to keep costs efficient.
Steps to Cloud Cost Optimization
- Monitor Usage: Track compute, storage, and network use to find underused resources.
- Right-Size Resources: Change instance types, storage, and databases to fit actual workloads.
- Use Auto-Scaling: Automatically scale resources up or down based on demand.
- Leverage Pricing Options: Use reserved, spot, or discounted instances when appropriate.
- Review & Optimize Regularly: Keep auditing architecture and change strategies to cut down waste.
40. What is zero-trust architecture?
Zero-Trust Architecture ZTA is a security model where no user, device, or system is trusted by default, even if they are inside the network perimeter. Every access request is verified, authenticated, and authorized continuously before granting access to resources.
41. What is a serverless architecture, and when is it beneficial?
Serverless architecture is a cloud computing model. In this model, developers write and deploy code without managing servers. The cloud provider takes care of infrastructure provisioning, scaling, and maintenance. This setup lets developers concentrate solely on application logic.
It’s is beneficial when :
- Variable or Unpredictable Workloads: Automatically scales for traffic spikes without pre-provisioning.
- Microservices and Event-Driven Systems: Ideal for small, independent functions triggered by events.
- Rapid Development: Developers focus on business logic instead of infrastructure.
- Cost Efficiency: Pay only for execution time rather than idle servers.
- Prototyping and MVPs: Quickly launch applications without investing in server setup.
42. Explain Difference between Data Lake and Data Warehouse.
Both Data Lakes and Data Warehouses are data storage systems, but they differ in structure, purpose, and use cases.
| Features | Data Lake | Data Warehouse |
| Definition | Data Lake is a centralized repository that stores raw, unstructured, semi-structured, and structured data at scale. | Data Warehouse is a system optimized for storing structured, processed data for analysis and reporting. |
| Data type | Raw data | Cleaned and structures data |
| Schema | Schema-on-read → structure applied only when data is read. | Schema-on-write → data structured before being loaded. |
| Flexibility | Highly flexible, it can store any type of data. | Less flexible, it can store only structured and relational data. |
| Users | Data scientists, ML engineers, big data analysts. | Business analysts, BI tools, decision-makers. |
| Costs | Generally cheaper storage | More expensive due to compute-heavy processing |
| Examples | AWS S3 + Athena, Azure Data Lake, Google Cloud Storage + BigQuery. | Amazon Redshift, Snowflake, Google BigQuery (as DW), Azure Synapse. |
43. What is rate limiting? Why is it important for security?
Rate limiting is a technique used to control the number of requests a user, system, or API can make within a specific time period.
Rate limiting is important for security to:
- Prevents DDoS attacks: It stops attackers from flooding a system with too many requests.
- Protects APIs from abuse: It ensures fair usage and prevents bots from overloading APIs.
- Reduces brute-force attacks: It slows down repeated login attempts and password guessing.
- Improves system stability: It prevents sudden traffic spikes from crashing servers.
- Ensures fair resource usage: One user can’t consume all resources at the expense of others.
44. How do you design architectures resistant to DDoS attacks?
- Edge Protection: Use a CDN, WAF, and provider DDoS services like AWS Shield or Cloudflare to absorb and filter harmful traffic before it reaches the app.
- Network Hardening: Apply security groups, SYN cookies, and protocol filtering to limit L3 and L4 floods.
- Rate Limiting and Bot Filtering: Enforce quotas per IP or per API key, and block unusual traffic patterns.
- Autoscaling and Caching: Make the application stateless where possible, enable auto-scaling, and cache static and dynamic content at the edge to reduce load on the origin.
- Graceful Degradation and Failover: Focus on critical paths, remove non-essential load, and use multi-region failover to keep availability during an attack.
45. What are Anti-Patterns in Microservices Architecture? How do you avoid them?
Anti-patterns are common mistakes or bad practices in microservices design that create problems like poor performance, tight coupling, or difficult maintenance.
How to Avoid Them
- Design for Loose Coupling: Each service should be independent.
- Database per Service: Use separate databases or schemas for clear ownership.
- Right-Sized Services: Split services based on what the business needs, not just technology.
- Use Async Communication: Prefer message queues or events instead of direct synchronous calls.
- Centralized Observability: Set up logging, tracing, and monitoring from the start.
- Follow Domain-Driven Design (DDD): Build around business areas.
46. What is Eventual Consistency?
47. What patterns do you use to ensure backward compatibility in APIs?
Backward compatibility in APIs ensures that existing clients continue to work even after new changes are introduced.
Patterns to Ensure Backward Compatibility in APIs
- Versioning: Use URI (/v1/users), query (?version=1), or header-based versioning.
- Additive Changes Only: Add new fields or endpoints without removing or renaming existing ones.
- Deprecation Policy: Mark old endpoints as deprecated but keep them functional for a transition period.
- Tolerant Readers: Design clients to ignore unknown fields and servers to provide default values for missing fields.
- API Gateway / Adapter Layer: Use middleware to translate requests/responses between old and new versions.
- Semantic Versioning & Documentation: Clearly communicate breaking vs non-breaking changes and maintain changelogs.
48. How do you implement Observability in a microservices ecosystem?
Steps to Implement Observability
- Collect logs from each service with contextual information (request ID, user ID, service name, timestamps).
- Centralize logs using ELK Stack (Elasticsearch, Logstash, Kibana), Splunk, or CloudWatch.
- Track system health metrics like latency, error rates, throughput, CPU, and memory usage.
- Use tools like Prometheus, Grafana, Datadog, or New Relic.
- Configure alerts for anomalies and SLA breaches.
- Implement tracing to follow requests across services and detect bottlenecks.
- Use OpenTelemetry, Jaeger, or Zipkin.
- Correlate traces with logs using unique correlation/request IDs.
- Aggregate logs, metrics, and traces into dashboards for real-time monitoring.
- Use dashboards for troubleshooting, root cause analysis, and capacity planning.
49. What are digital twins?
From a Solution Architect’s perspective, digital twins are part of complex system design, combining IoT, cloud, analytics, and AI/ML to mirror and optimize physical assets or processes. The architect’s role is to design a scalable, secure, and maintainable digital twin ecosystem.
50. How would you design systems that use AI like ChatGPT?
Designing systems that integrate AI models like ChatGPT requires a combination of scalable architecture, API integration, data handling, and security. As a Solution Architect, the focus is on reliability, performance, and maintainability.
Key Design Considerations are:
- Define Use Case: Identify AI's purpose and integration points.
- Model Integration: Connect through APIs or dedicated infrastructure with retries and batching.
- Scalable Architecture: Use stateless microservices, load balancers, and auto-scaling.
- Data Management: Handle inputs and outputs securely, encrypt data, and follow privacy rules.
- Observability: Monitor latency, errors, token usage, and user interactions.
- Security and Access Control: Enforce authentication, set rate limits, and validate inputs.
- User Experience: Set up feedback loops and, if needed, include human-in-the-loop review.
Conclusion
Preparing for a Solution Architect interview requires more than just technical knowledge, it demands a clear understanding of system design principles, architectural patterns, scalability, security, and emerging technologies.
Become a high-paying Java Solution Architect, master microservices, design patterns, and cloud integration today! Enroll now in Java Solution Architect Certification. Also, If you want to Future-proof career in .NET—Enroll in our .NET Solution Architect Certification and master enterprise-level architecture.





